Tactic 25. Defensive Tactic – Change & Escalate Peering Prerequisites
In this tactic, the ISP adjusts the peering prerequisites as other ISPs approach meeting them. Once the peering requirements have been met, the ISP simply adjusts them upwards (Figure 11-39).
In the community, this tactic is recognized as simply an implementation of a restrictive Peering Inclination, a general inclination not to peer with anyone else.
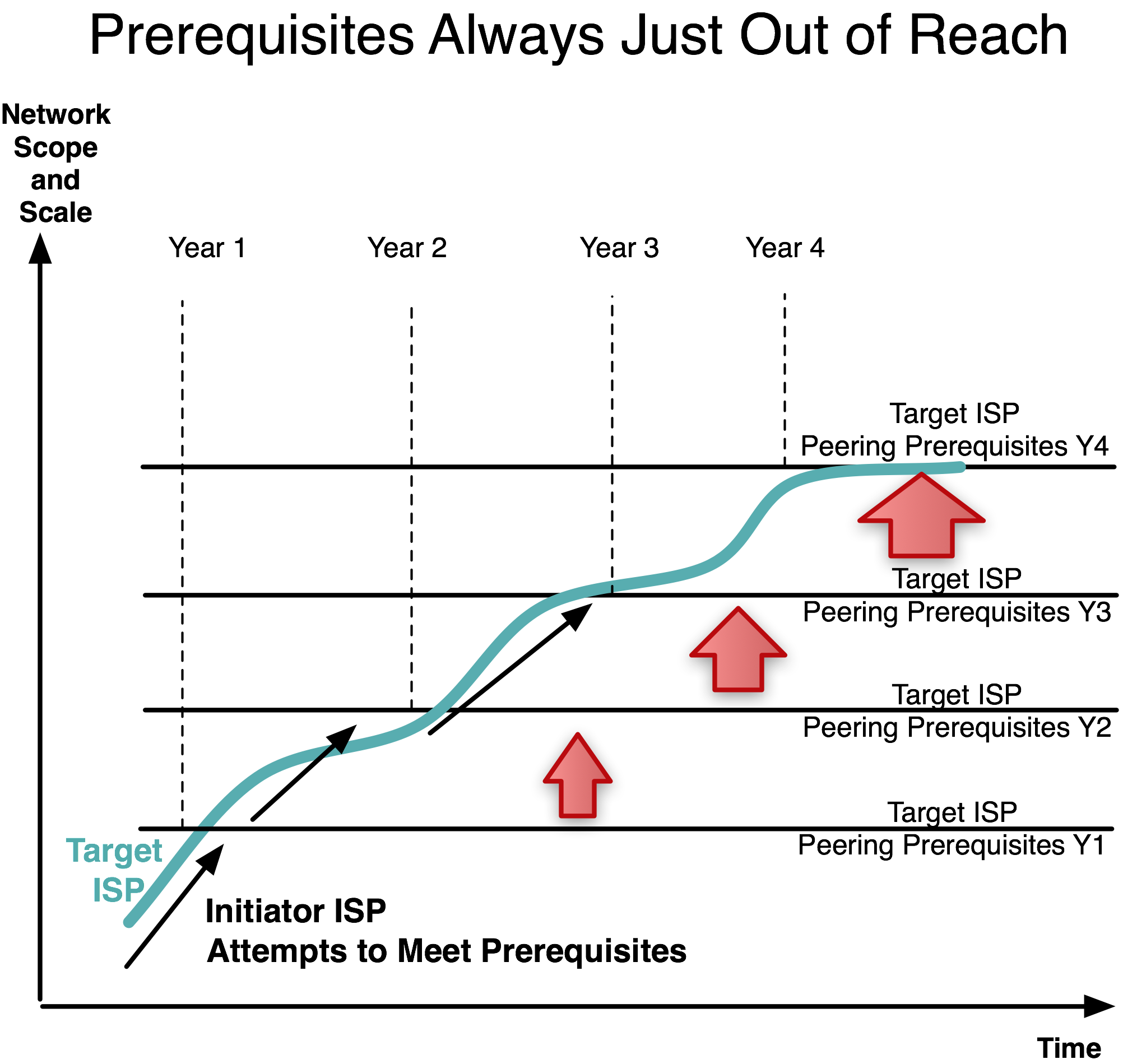
Figure 11-39. Adjust peering requirements over time.

