Tactic 26. MILD Defensive Tactic
The following story was told earlier, in Chapter 9, to highlight the way an ISP’s Peering Inclination may differ from its stated Peering Policy. It is repeated here as a Defensive Tactic:
At an APRICOT conference, James Spenceley (Comindico) shared a tactic that Telstra executed in Australia. Comindico met with Telstra to demonstrate that it had met the very difficult-to-meet peering prerequisites. Spenceley characterized these requirements as “bringing enough capacity into the territories for many Mbps for every man, woman, child, and kangaroo.” Once Comindico had built its transcontinental backbone, the network maps were exchanged as part of the peering discussion. Ultimately, the peering requirements were changed such that Comindico only slightly failed to meet them.
Comindico went bankrupt shortly thereafter.
It is possible that the adjustments of the peering requirements were merely a coincidence (they do change), and the story came to me second-hand, so we must allow for the possibility that there is another side to the story.
However, we have heard stories about this tactic before. Several other large Tier 2 ISPs in different parts of the world have identified this maneuver being perpetrated by the Tier 1 ISPs in the field.
The MILD tactic stands for Make It Long and Difficult. James Spenceley perhaps coined the phrase for this tactic (Figure 11-40). The approach is to prolong the peering discussions so that while you appear to be open to peering, the process never ends, and effectively peering will never happen.
To play out the example in slightly more detail, once the peering requirements are met, the peering candidate notifies the Tier 1 that it would like to meet to discuss peering. The response is that the request is being considered. Several months later a follow-up request results in an in-person meeting – scheduled for several months later. At that meeting additional documentation is requested and a follow-up meeting is scheduled for several months later. These meetings are rescheduled a few times. When the parties reconvene, there is a new team that has to be brought up-to-speed on the peering discussions, further delaying the execution of peering. Additional questions are extended to the potential peer.
During this stretched-out discussion in Australia, Comindico was paying for an overbuilt network that exceeded its revenue. As stated before, it appears that ultimately this situation led to Comindico’s bankruptcy.
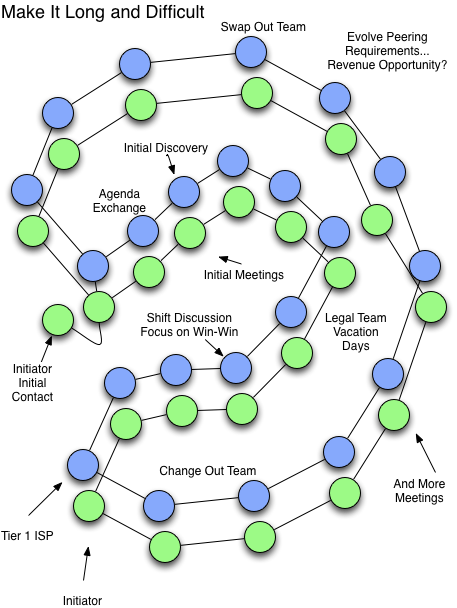
Figure 11-40. The MILD defensive tactic is intended to neither provide nor deny Internet Peering requests.

